How to Add a CDN to Your No-Code App
Learn how to add a CDN to your no-code app: pick a provider, update DNS and cache settings, version assets, and test performance.

Learn how to add a CDN to your no-code app: pick a provider, update DNS and cache settings, version assets, and test performance.
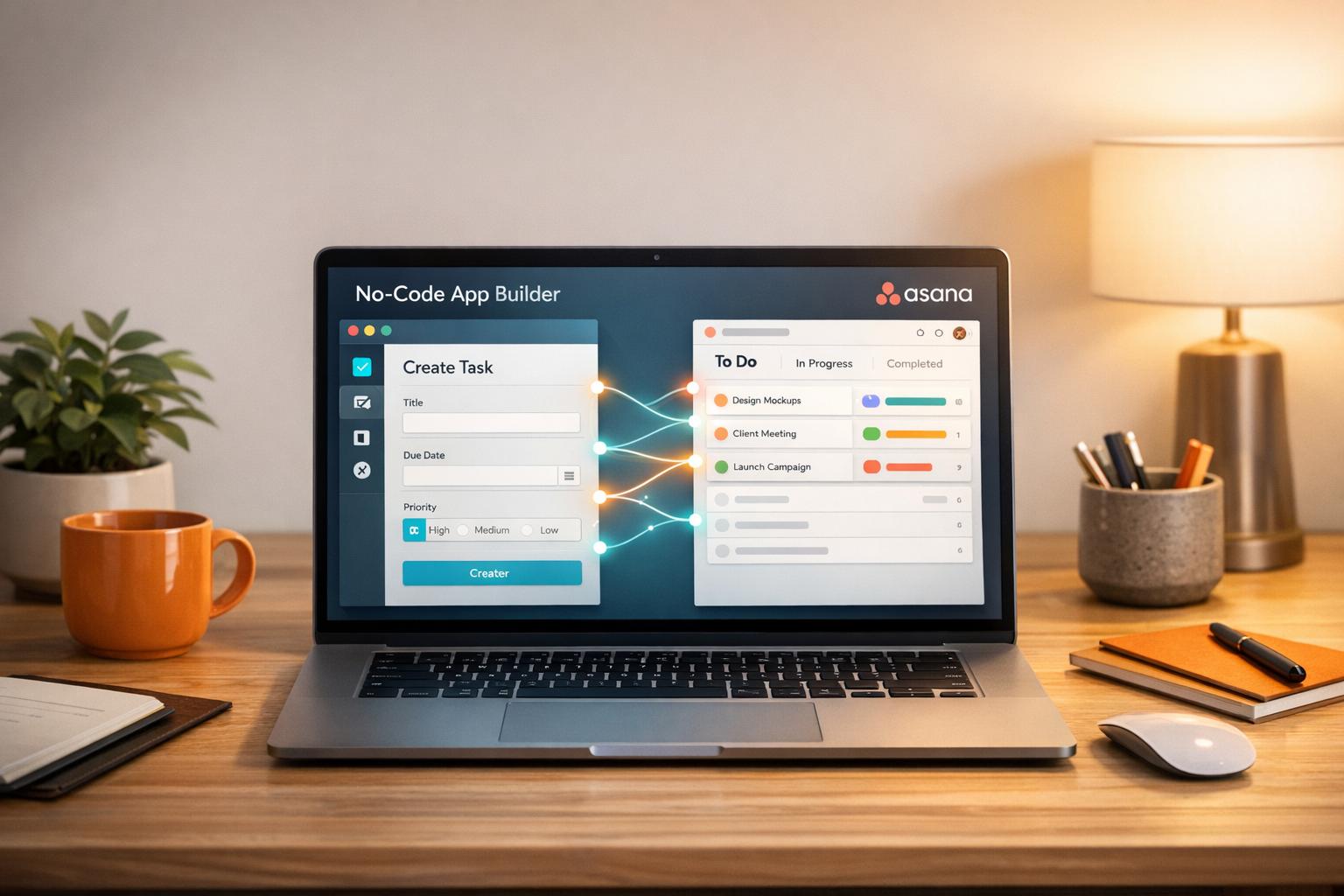
Step-by-step guide to link a no-code app with Asana using a Personal Access Token, map fields, set triggers, test, and fix common integration issues.
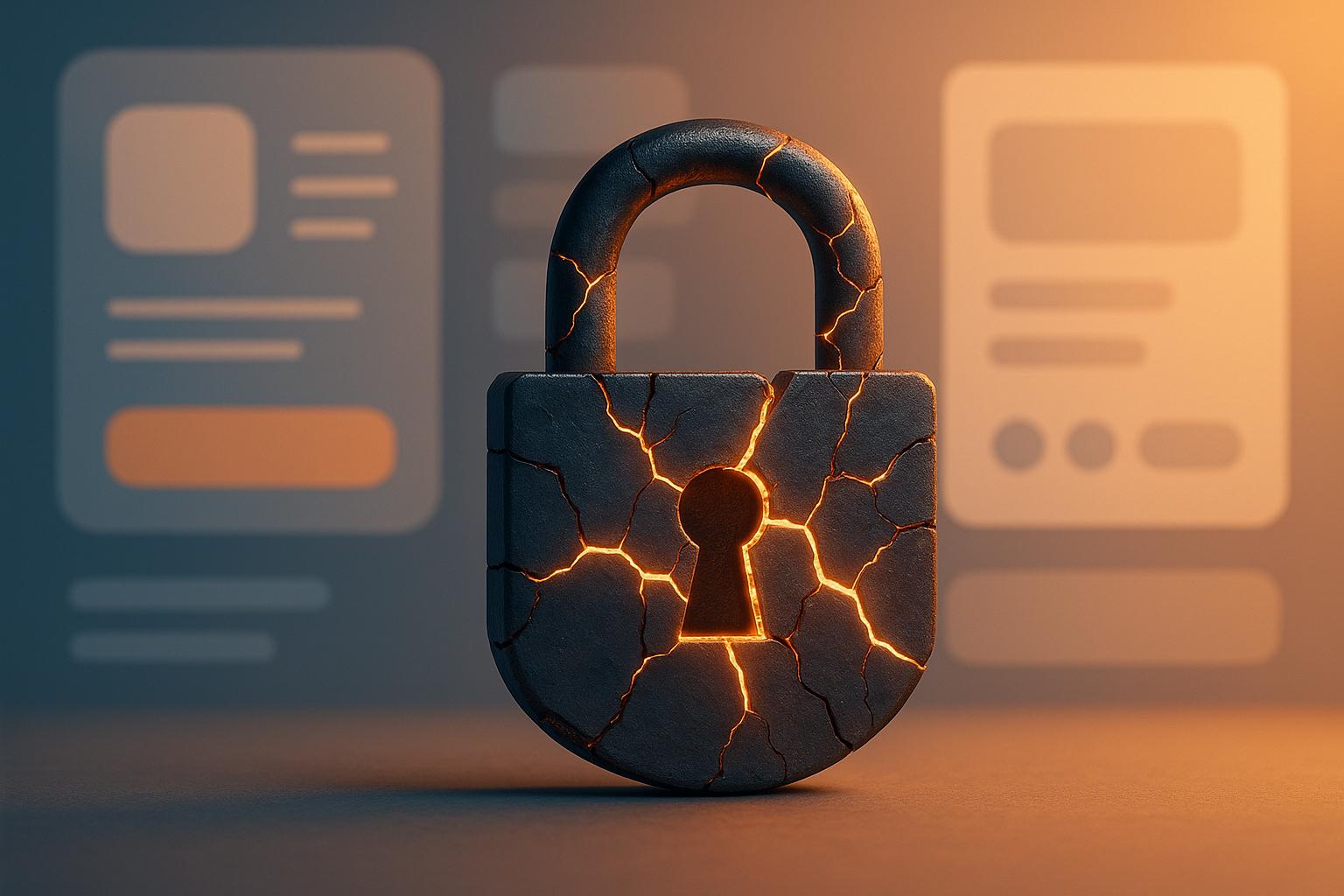
No-code platforms simplify app development but pose serious security risks. Learn to protect sensitive data and avoid vulnerabilities effectively.

Author: Area Martion Let me take you back to when I first started my journey as a content writer. I was excited, full of energy and honestly a bit too confident. I believed that writing was just about having good grammar and a fancy vocabulary. But I quickly learned that writing for the web, especially…
Read More

To manage a busy and competitive restaurant, having the correct instruments is necessary for smooth service and content customers. A restaurant needs to have a reliable point-of-sale system as a top priority. There’s more to a restaurant POS system than only handling payments. It is at the center of operations, controlling orders, inventory, how staff…
Read More

Many people believe a VPN hides everything about them online. They think their IP address no longer matters. VPNs mask your real IP by routing traffic through other servers. But your IP address can still expose important information. Even with a VPN, some leaks happen. Websites or apps can detect your real IP through flaws,…
Read More
The world of software houses is always on the move. These businesses operate at a very fast pace, with deadlines to meet, testing to do, and projects to deliver. All these tasks demand high productivity under tight schedules. Yet, unclear task tracking and manual billing processes hinder performance and profitability. In such environments, accurately measuring…
Read More

Legacy systems refer to old, outdated computer systems, applications, languages, and databases that are still being used by organizations to run critical business functions. These systems were created years ago using technologies that are now considered obsolete. However, many companies rely heavily on legacy systems for vital operations and are reluctant to replace or modernize…
Read More

Technological upgrades are essential for maintaining a competitive edge and operational efficiency in the rapidly evolving digital landscape. However, the cost associated with significant technological improvements can be a substantial barrier for many businesses. This is where a business line of credit enters the picture. It offers a flexible financing solution to help companies manage…
Read More
https://www.pexels.com/photo/flat-screen-computer-monitor-1714340/ With the current trends of rapid growth and diversification of information technology, cloud computing has emerged as the central pillar for organizations in terms of flexibility, expansiveness, and effectiveness. Outsourcing has gone beyond an option to a reality, with many organizations having to shift to cloud services. Although it may be a…
Read More